WordPress currently powers more than 43% of the sites on the internet in 2025. While that says a lot about its flexibility, great library of plugins, and robust ecosystem, it also makes WordPress a massive target for hackers. Brute-force login attempts, malware injections and plugin vulnerabilities are some common threats to WordPress websites, and the situation is only getting worse.
If you’re asking yourself the question – “How do I secure my WordPress website?, you’re not alone. As a site owner, developer, or IT professional, WordPress security falls on your shoulders, and you’re responsible for protecting your site from countless vulnerabilities.
In this blog we will cover our top 25 tips and wordpress security checklist around authorization, malware scanning, access management and plugin-dependency that’ll help you keep your game sharp well into 2025 and beyond.
Why WordPress Websites Get Hacked
WordPress is Open Source, customisable and popular, which is a bad combination for attracting hackers. The following issues are often exploited:
- Outdated plugins or core files with unresolved vulnerabilities
- Weak login credentials like “admin” or “123456”
- Poor firewall configurations or lack of web application firewalls
- Uncontrolled user permissions or unnecessary admin access
Here are the practices you can follow to secure your wordpress website from hackers.
25 Security Best Practices to Secure WordPress in 2025
We have compiled checklist of wordpress security best practices that can help you secure your website confidently.
1. Keep WordPress Core, Plugins, and Themes Updated
A weak plugin is usually the reason of for malware to be created in your website. Updates often contain important security fixes that address known flaws, and delaying updates only gives hackers more time to exploit those holes. Keep everything up to date and use plugins with good historical patching and developer participation. Use staging environments to assess sensitive changes before implementing them on live environments.
2. Choose a Secure Hosting Provider
Your web host is really your first defence. If that is the case, try to find managed WordPress hosts that include firewall integration, malware scanners, SSL, DDoS protection, backups, etc. Also confirm the host is running current server software, like PHP and MySQL. Good hosts will also offer customer support that can handle breakin attempts as they happen.
3. Use Strong Usernames and Passwords
Credential stuffing and brute force attacks excel with weak credentials. Protect your login area by having strong, unique passwords and not using predictable usernames, such as an admin username. Leverage a password manager that will create and save credentials. Combine this with access control policies to ensure that only essential users have elevated permissions.
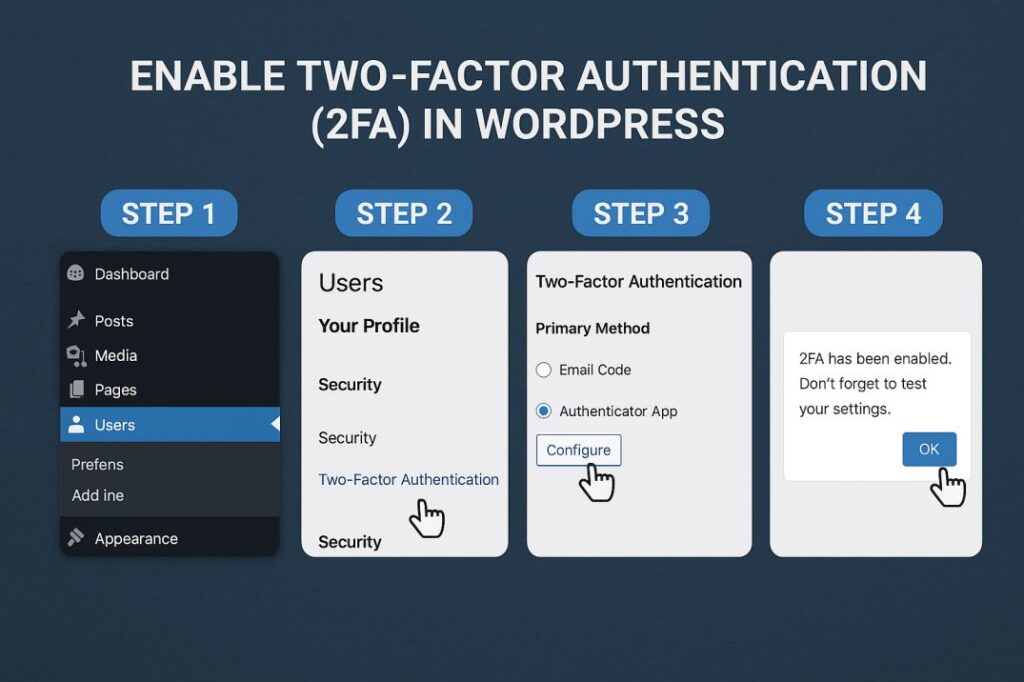
4. Enable Two-Factor Authentication (2FA)
Passwords can be guessed or stolen; 2FA adds an extra verification step using a secondary device or app. Enable it for all admin users and recommend it for all others. Plugins such as Wordfence Login Security or integration with Google Authenticator will make it painless to use. This significantly lowers the risk of unauthorized entries when passwords are hacked.
5. Limit Login Attempts
Prevent brute force attacks by setting maximum number of failed attempts to login. Although plugins like Limit Login Attempts Reloaded or Jetpack’s brute-force protection module ban IPs after a number of unsuccessful logins. You can also control IP lockouts and generate email notifications about suspicious login attempts to keep yourself updated.
Here’s the most easiest and recommended method to limit login attempts
Go to Plugins > Add New
- Search for Limit Login Attempts Reloaded
- Install and activate the plugin
- Go to Settings > Limit Login Attempts
- Configure:
- Allowed retries (e.g., 3)
- Lockout duration (e.g., 20 minutes)
- Increase lockout time after multiple failure.
6. Change the Default Admin Username
Not only will using “admin” as your username put a target on your site for bots, but it’s also just not secure. Create a new admin account with a different username and delete the original one. This cuts down considerably on the chance of automatic login attempts being successful.
7. Enable HTTPS/SSL
SSL certificates work by encrypting the data exchanged between your server and the user browser. Obtain free SSL certificates with Let’s Encrypt and configure your WordPress installation to redirect all traffic through HTTPS. It prevents data from being intercepted and provides users with more confidence in the site. In addition, possessing an active SSL certificate is a must-have ranking factor on Google SEO algorithm, whereby secure sites are preferred in search results.
8. Install a Security Plugin
Security plugins act as a multi-functional security toolkit. You have firewall rules, malware scanning, login protection, and alerts for threats provide by Wordfence, Sucuri, and Jetpack Security. Go ahead and pick one according to your technical comfort and make sure it is set up correctly.
9. Disable File Editing in Dashboard
File editing through the admin panel is a major security risk. Disable it by adding this to wp-config.php:
define('DISALLOW_FILE_EDIT', true);This prevents attackers from injecting malicious code if they gain admin access.
10. Restrict Access to wp-admin
Protect the admin area with an extra password layer or IP-based access control. Use .htaccess rules or server-side protections to lock it down. On shared hosting, cPanel’s Directory Privacy feature adds another login prompt before reaching wp-login.php.
11. Set Correct File Permissions
Use these recommended settings:
- 755 for directories
- 644 for files
- 400 or 440 for wp-config.php
These settings prevent unauthorized file changes and reduce the damage if an attacker gains access.
12. Use a Web Application Firewall (WAF)
WAFs filter incoming traffic to prevent malicious requests like SQL injection, XSS, or CSRF. For better performance and extra layer of protection, use plugins like Sucuri or go for a CDN based WAF like Cloudflare.
13. Limit User Permissions
Assign roles according to necessity. Editors or Authors don’t need admin access. Use plugins like User Role Editor to fine-tune permissions. Excessive permissions increases your attack surface.
14. Regularly Scan for Malware
Perform automated and manual scans to detect malicious scripts, spam links, or backdoors. Schedule these scans through your security plugin. Early detection prevents SEO penalties and data loss.
15. Automate and Offload Backups
Backups are essential for disaster recovery. Use plugins like UpdraftPlus, BlogVault, or Jetpack Backup to automate and offload backups to Google Drive or Amazon S3. Schedule daily or real-time backups and regularly test restore functionality.
16. Disable XML-RPC and Directory Indexing
Disable XML-RPC to prevent bots from abusing it for brute-force or DDoS attacks:
<Files xmlrpc.php>
Order Deny,Allow
Deny from all
</Files>
Also disable directory listing with:
Options -Indexes
17. Change Default Database Prefix
SQL injection tools often target tables with the default “wp_” prefix. Change it during installation or use security plugins to safely rename the prefix on existing installs.
18. Harden wp-config.php and .htaccess
Protect sensitive files by denying external access:
<files wp-config.php>
order allow,deny
deny from all
</files>
<files .htaccess>
order allow,deny
deny from all
</files>
19. Update PHP and Server Stack
Security doesn’t stop at WordPress. Keep your hosting environment updated with the last supported versions of PHP, MySQL, and web server software. Old stacks leave your site vulnerable to system-level issues.
20. Add CAPTCHA to Login and Forms
Add reCAPTCHA to your login form, comment form, and contact form to prevent bots. Integrate it via plugins such as WPForms or Advanced Google reCAPTCHA.
21. Hide Login URL and Whitelist IPs
Change your login URL from wp-login.php using plugins like WPS Hide Login. Combine this with IP whitelisting to restrict access to known addresses.
22. Disable PHP Execution in Uploads Folder
Prevent attackers from executing scripts in your media folder by adding this .htaccess rule to wp-content/uploads:
<Files *.php>
deny from all
</Files>
23. Monitor Activity Logs
Track user actions and file changes using activity log plugins like WP Activity Log or Simple History. These logs help identify suspicious behavior early.
24. Use AI-Powered Threat Detection
Next-gen plugins are using AI to detect anomalies and any potential zero-day attacks. Intelligent scanning engines from Wordfence and Sucuri can adapt to learn new attack patterns.
25. Harden Server-Level Security
Harden your server using tools such as Fail2Ban, mod_security and firewall rules. Prevent root sign in through SSH and set up key-based access if possible.
Wrapping Up
When it comes to securing your WordPress site, then it is not a one-time thing to do, but an ongoing process. In 2025, as cyber threats help elevate incredibly, the best means to safe website is included multi-layered safety technique.
These 25+ best practices are not just a way to mitigate risks, they are the building blocks of a faster, more secure website, your users will love. Need assistance in implementing those changes or looking for a comprehensive security and performance examination?
WebCreativz provides a wide range of expert-level WordPress maintenance, malware removal, and performance optimization services that can be tailored to your specific functionality.
Call us today to get your site secure and running as quickly as possible!

